GCP + Cloudflare: Eliminating 522/523/524 Errors for Windows VM Workloads
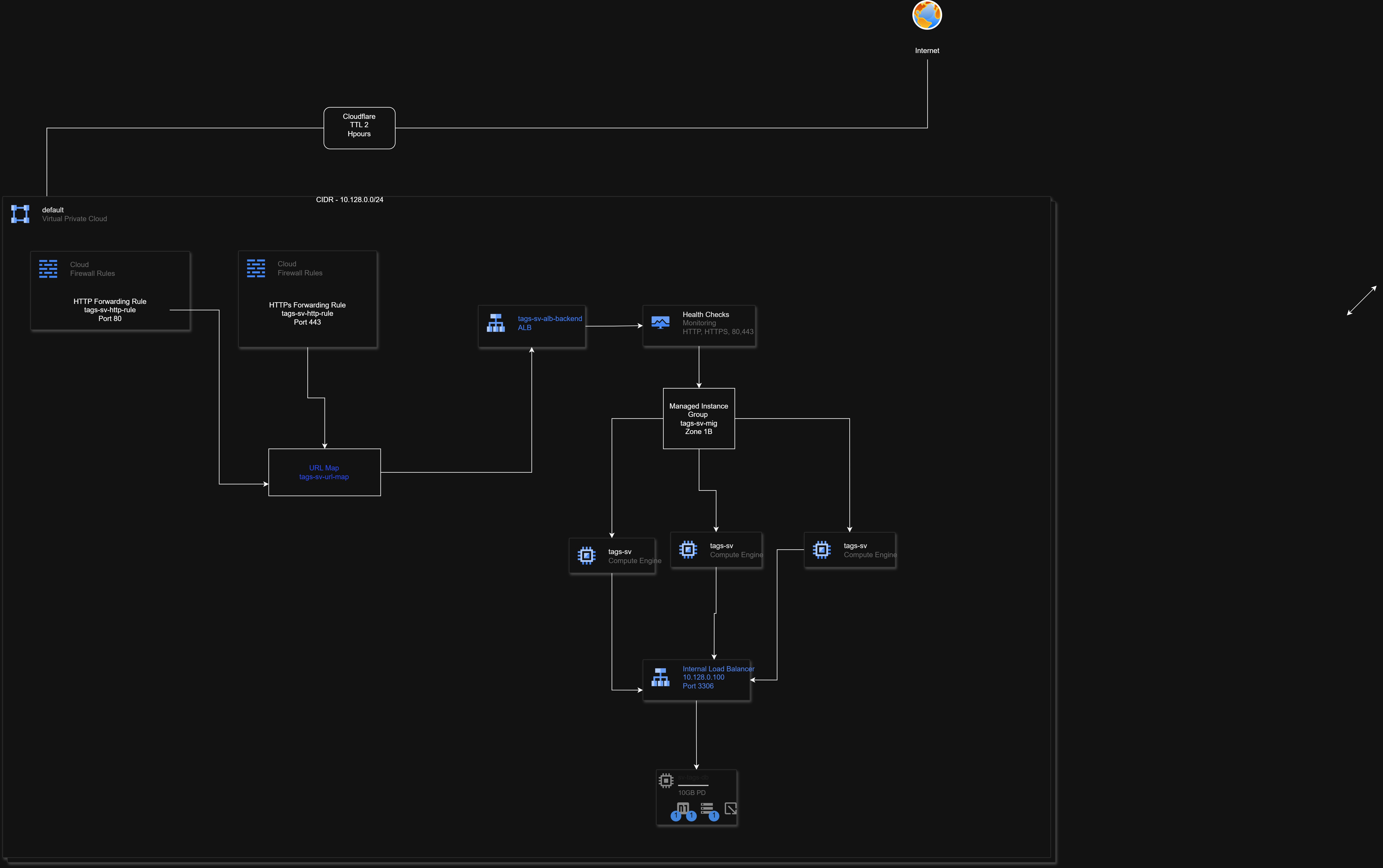
Project architecture: Cloudflare CDN, GCP Load Balancer, Managed Instance Groups, Health Checks, Internal DB LB, Windows VMs
Project Overview
Challenge:
A SaaS client was experiencing persistent Cloudflare 522, 523, and 524 errors on their public-facing applications hosted on Windows VMs in Google Cloud Platform (GCP). These errors, typically caused by slow server response or network bottlenecks, resulted in intermittent outages, degraded user experience, and lost business opportunities—especially during high traffic or Windows update cycles.
Root Causes Identified:
- Server Overload: Windows VMs under heavy load or during patching would respond slowly or not at all, triggering Cloudflare timeouts.
- Firewall Misconfiguration: Incomplete allow-lists for Cloudflare’s IP ranges and health check probes caused legitimate traffic to be dropped.
- Improper Load Balancing: Lack of intelligent health checks and failover meant that unhealthy VMs were still receiving traffic, compounding downtime.
- Database Bottlenecks: Direct database connections from application VMs without internal load balancing led to performance issues under concurrent access.
Solution Architecture
- Cloudflare CDN & Proxy: Acts as the global entry point, providing DDoS protection, caching, and SSL termination with a 2-hour TTL for rapid DNS propagation.
- GCP VPC (10.128.0.0/24): Secure, isolated network segment for all resources.
- HTTP(S) Load Balancer: Handles all inbound HTTP/HTTPS traffic, with forwarding rules for ports 80 and 443.
- URL Map: Directs traffic to the correct backend services and enables path-based routing.
- Managed Instance Group (MIG): Auto-scales Windows VM instances across zones, ensuring redundancy and high availability.
- Health Checks: Regular HTTP/HTTPS probes (ports 80/443) to verify VM responsiveness before routing traffic.
- Internal Load Balancer: Balances MySQL (port 3306) traffic for backend database access, isolating DB workloads from public exposure.
- Firewall Rules: Explicitly allow Cloudflare IP ranges and health check probes, blocking all other unnecessary traffic for maximum security.
Implementation Highlights
- Zero Downtime During Updates: Managed instance groups and rolling updates ensured Windows patches no longer caused outages. Unhealthy or rebooting VMs were automatically drained from the load balancer.
- Proactive Health Monitoring: Custom health checks on both HTTP and HTTPS ensured only responsive VMs served live traffic.
- Firewall Hardening: Only Cloudflare and Google health check IPs were permitted, eliminating accidental blocks and reducing attack surface.
- Database Performance: Internal load balancing for MySQL traffic prevented single points of failure and improved query response times.
- Scalability: The solution auto-scales horizontally based on load, ensuring performance during traffic spikes.
Results & Business Impact
- 522/523/524 Errors Eliminated: The client’s users no longer experienced Cloudflare connection timeouts, even during peak load or server maintenance windows.
- 99.99% Availability: The application maintained near-perfect uptime, with seamless failover and zero visible downtime during VM updates or failures.
- Improved Security: Strict firewall rules and Cloudflare’s DDoS protection reduced attack vectors and mitigated volumetric threats.
- Operational Efficiency: Automated scaling and self-healing minimized manual intervention, freeing up the client’s IT team for higher-value tasks.
- Documented & Repeatable: The entire architecture and runbooks were delivered for the client’s future scaling and onboarding needs.
Key Takeaways
- Cloudflare errors like 522/523/524 are almost always rooted in origin server or network issues, not CDN misconfiguration.
- Proactive health checks, proper firewall rules, and managed load balancing are essential for resilient cloud applications.
- Automating server patching and scaling is critical for Windows-based workloads in the cloud.
- A layered approach—combining CDN, cloud-native load balancing, and strict security—delivers both reliability and performance.
Need help with GCP, Cloudflare, or solving similar errors?
Contact me for a consultation →